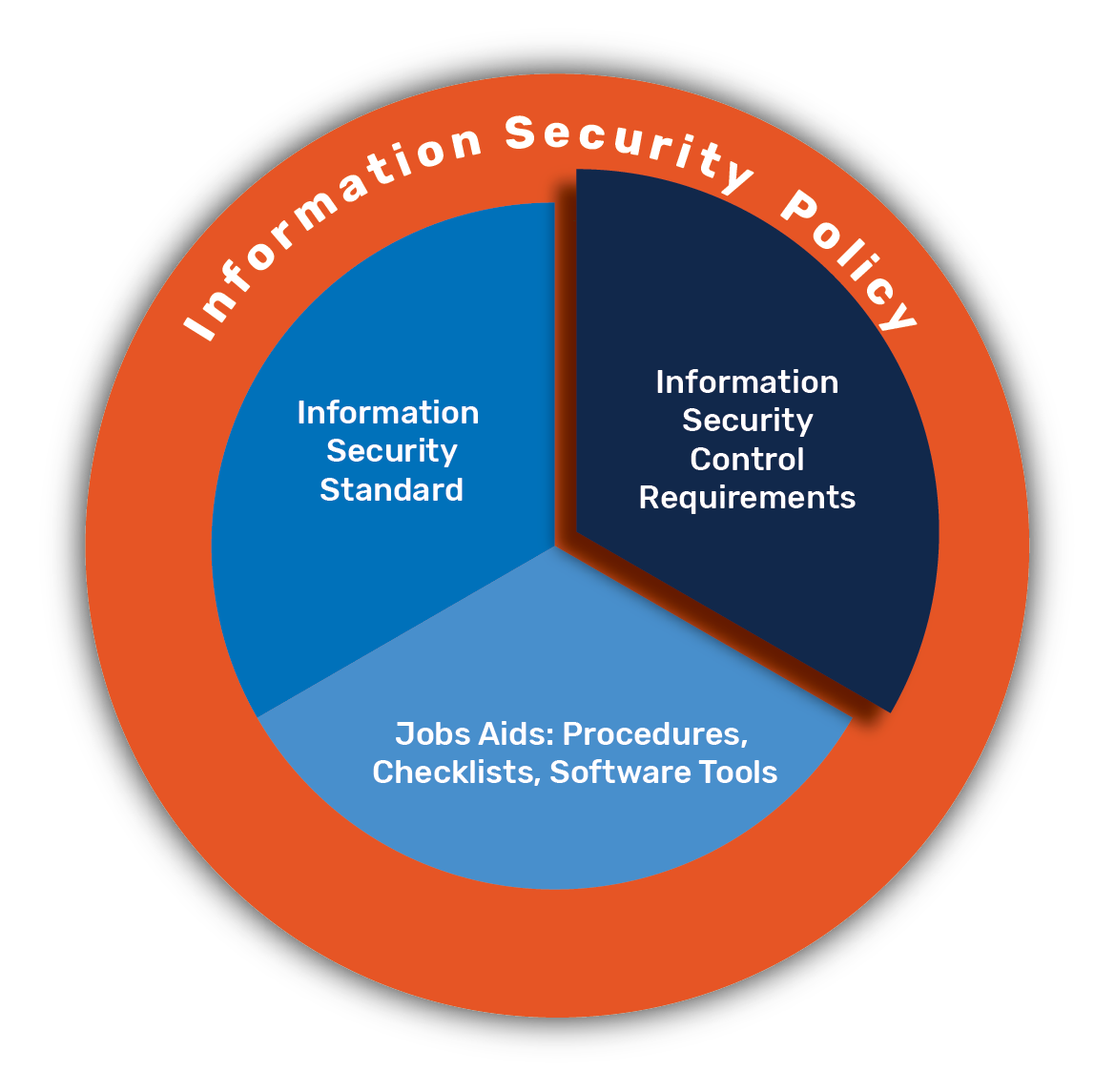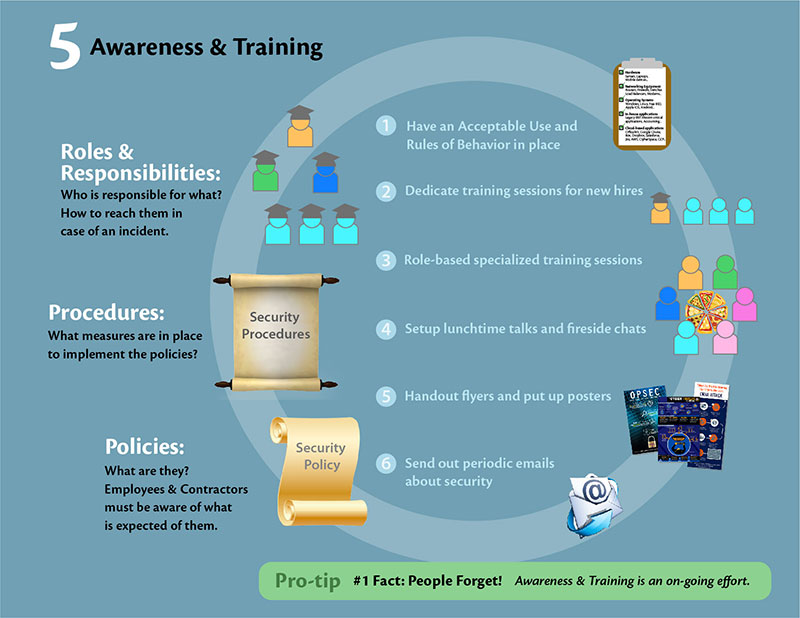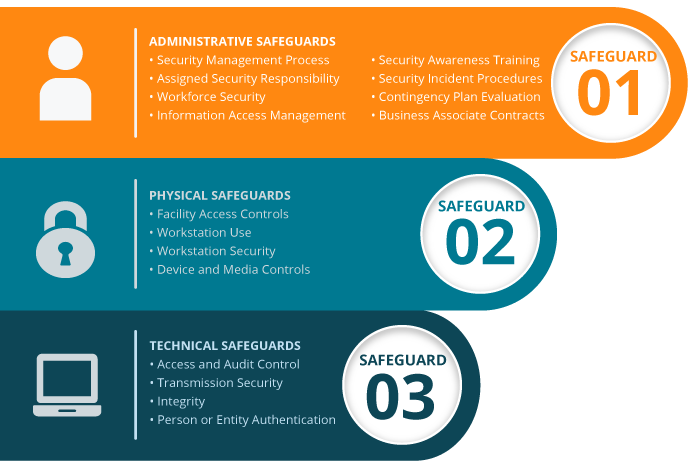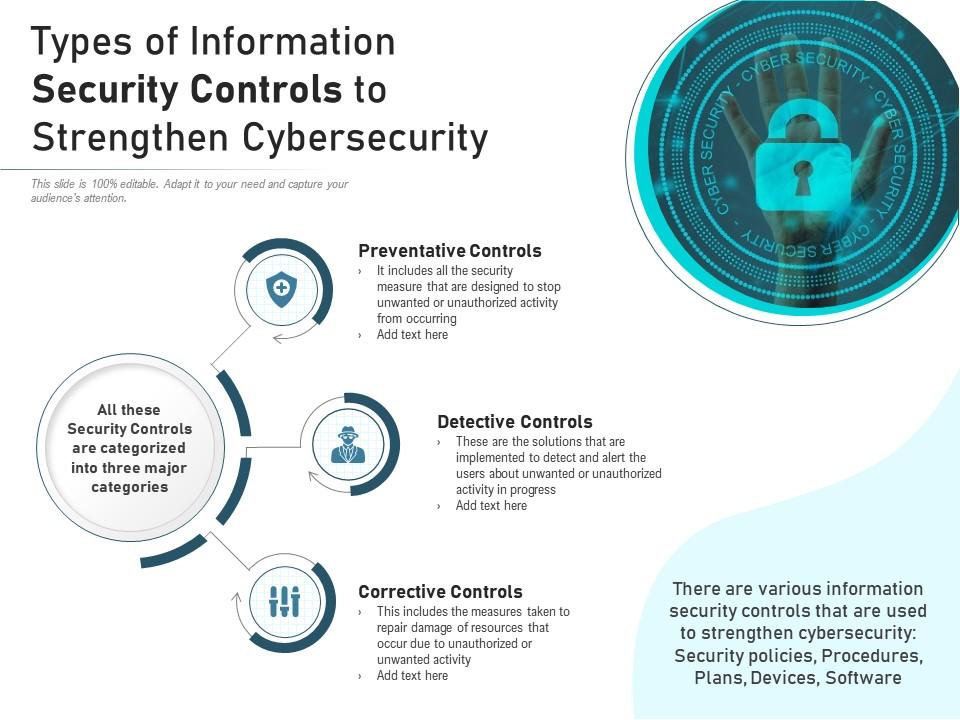
Types Of Information Security Controls To Strengthen Cybersecurity | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

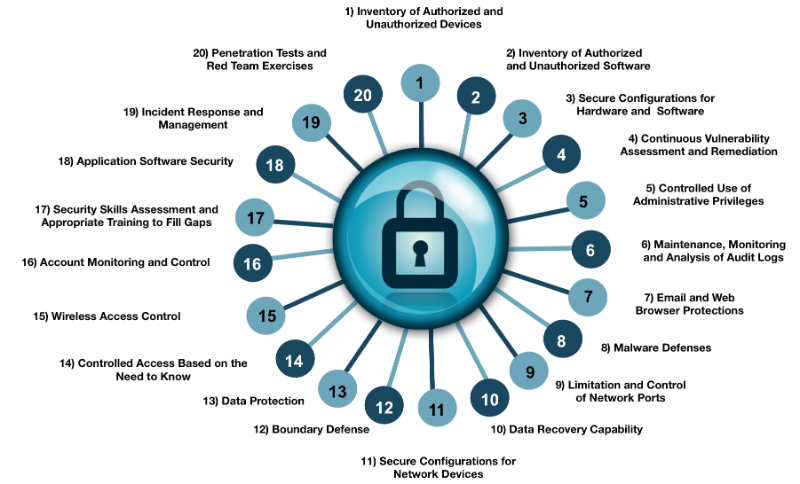
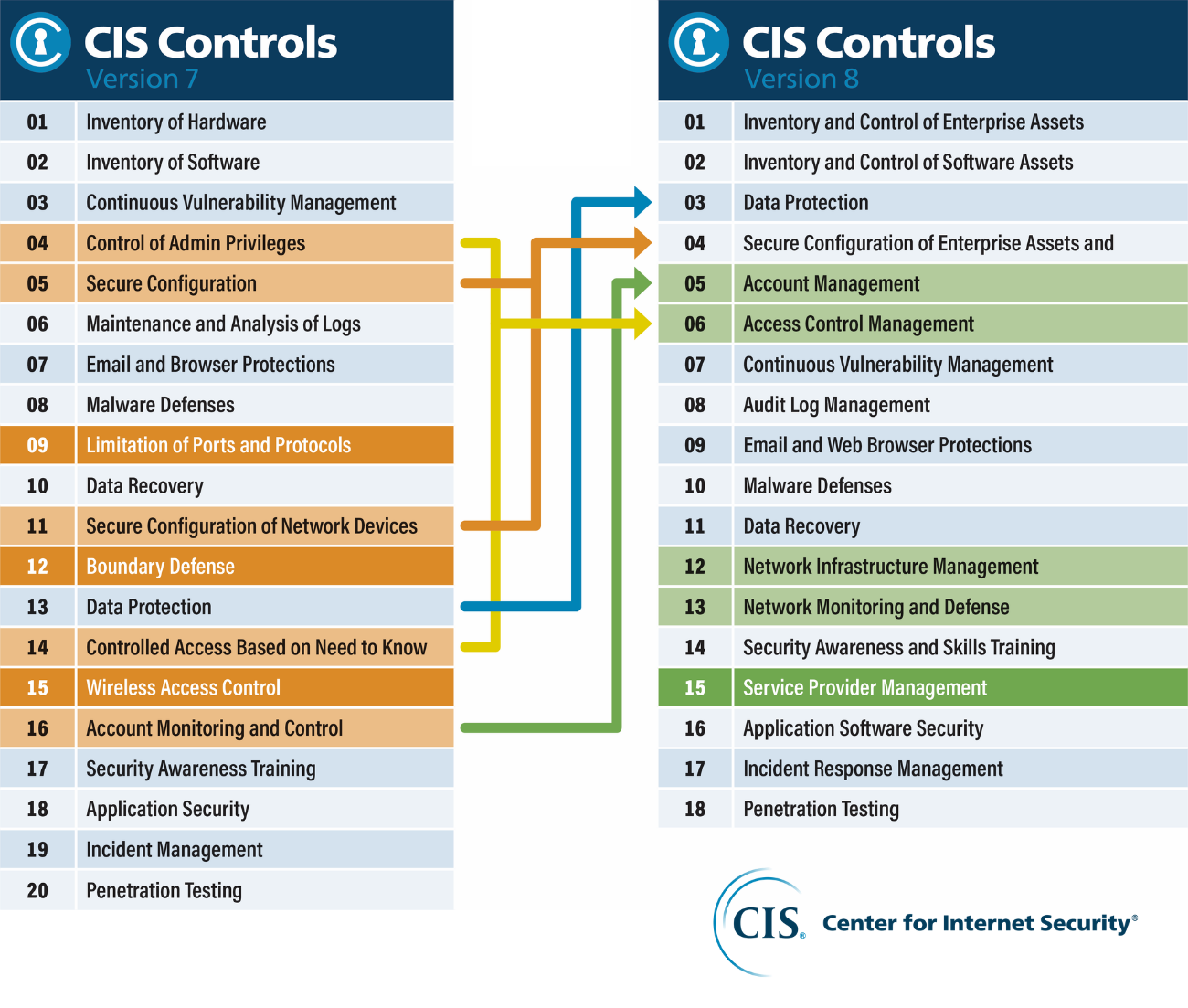
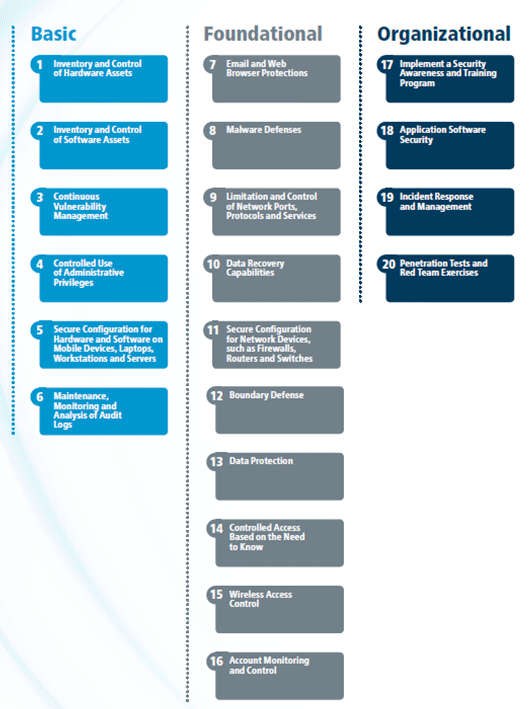
CIS Critical Security Controls – Six “Basic” Strategies to Deliver Immediate and Effective Cyber Defense - Valeo Networks

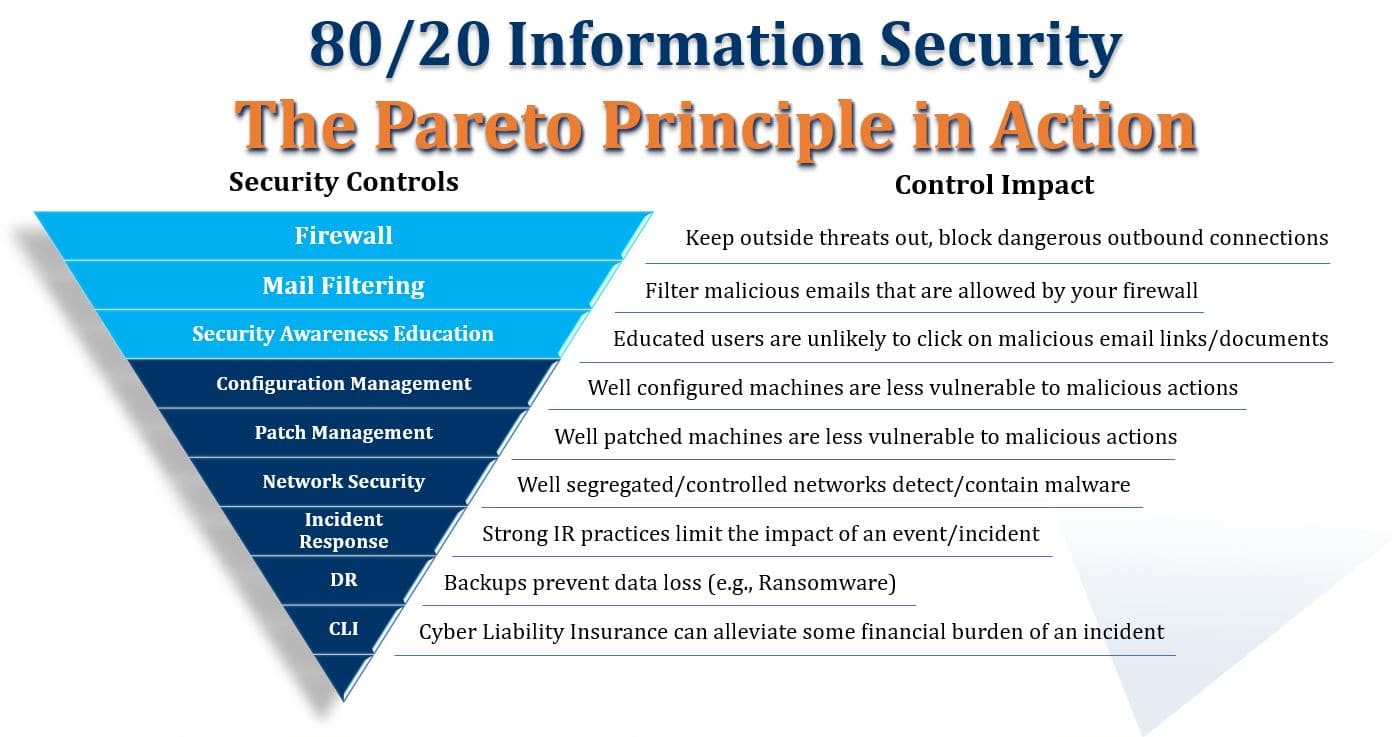
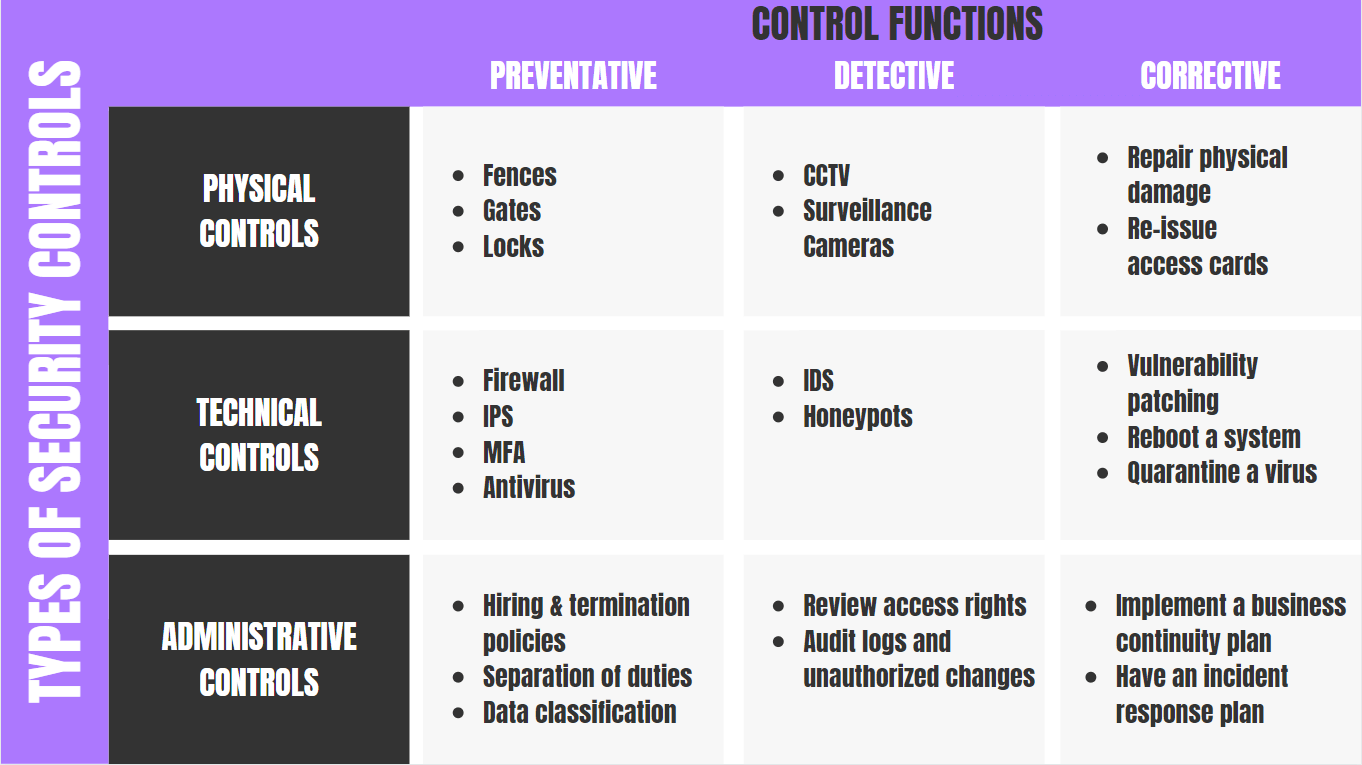
Tabular Presentation Of Security Controls Categorization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
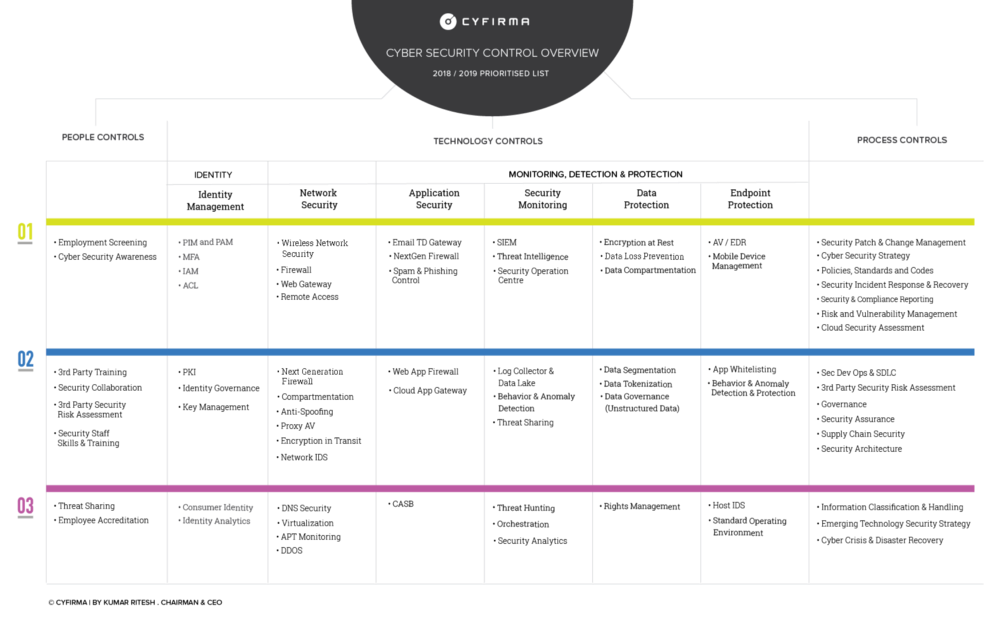
Transportation Management Center Information Technology Security - Chapter 3. Best Practices for Traffic Management Centers Information Technology Security - FHWA Office of Operations